AWS Incident Response - Cloud Trail Logs
Respond to an AWS security incident by analyzing cloud trail logs.
This is a walkthrough for "Bucket" by CyberDefenders
Scenario
Video Walkthrough:
Welcome, Defender!
As an incident responder, we're granting you access to the AWS account called "Security" as an IAM user. This account contains a copy of the logs during the time period of the incident and has the ability to assume the "Security" role in the target account so you can look around to spot the misconfigurations that allowed for this attack to happen.
#1
- What is the full AWS CLI command used to configure credentials?
- An Access Key and Secret Key are provided for this challenge so I’ll go ahead and configure a profile using these credentials
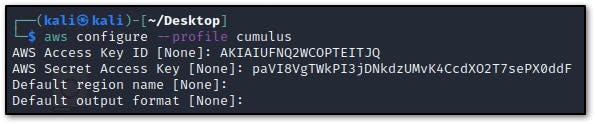
- Confirm “security” IAM user as specified in the scenario
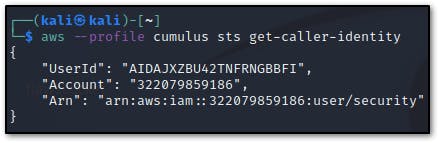
- aws configure
#2
- #2 What is the 'creation' date of the bucket 'flaws2-logs'?
- Check for the bucket creation date using the s3api
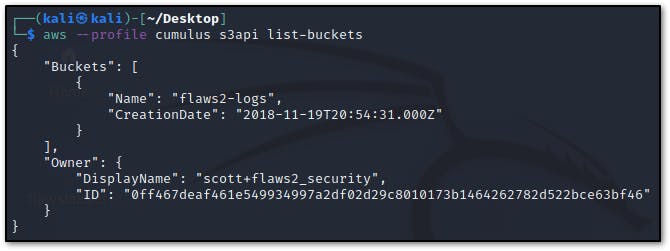
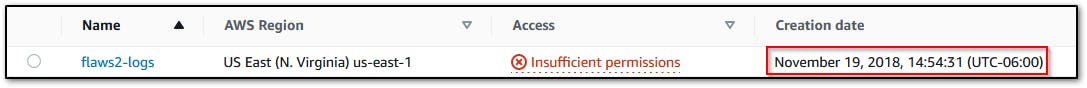
- 2018-11-19 20:54:31 UTC
#3
- #3 What is the name of the first generated event -according to time?
- Dump bucket data (logs) to local directory
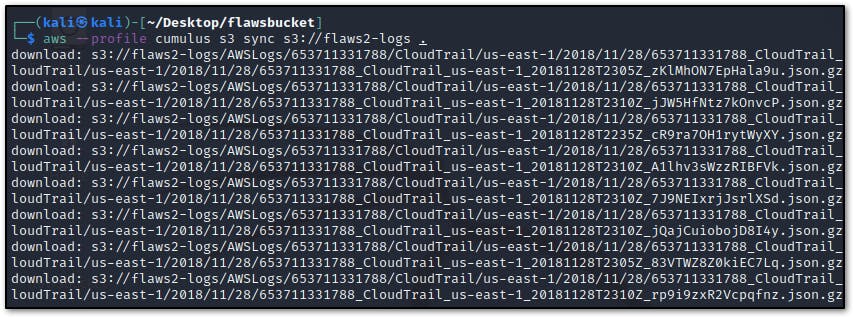
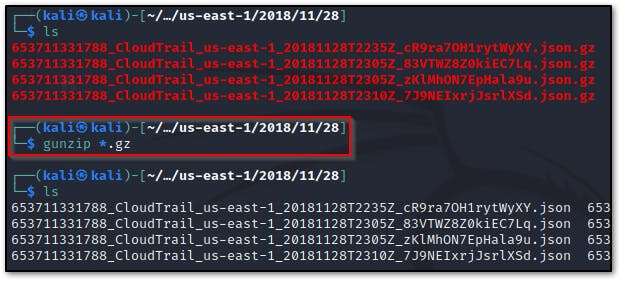
- unzip the
.jsonfiles
- view one json file
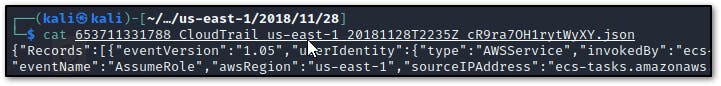
format is hard to read so install jq for JSON
sudo apt install jqview again..much better
- create a shell script that searches all files and filters by EventTime
#!/bin/bash LOGS="*.json" #specifying the variable for logs for l in $LOGS # starting the for loop do echo "Analyzing $l" # analyzing the log file cat "$l" | jq | grep eventTime # displaying the eventtime in JSON format cat "$l" | jq | grep eventName # displaying the eventname as well done- execute the script
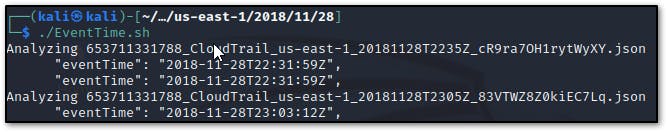
- The observed first event is from
653711331788_CloudTrail_us-east-1_20181128T2235Z_cR9ra7OH1rytWyXY.jsonwhich is observed with the “AssumeRole” eventName
Analyzing 653711331788_CloudTrail_us-east-1_20181128T2235Z_cR9ra7OH1rytWyXY.json "eventTime": "2018-11-28T22:31:59Z", "eventTime": "2018-11-28T22:31:59Z", "eventName": "AssumeRole", "eventName": "AssumeRole",- AssumeRole
#4
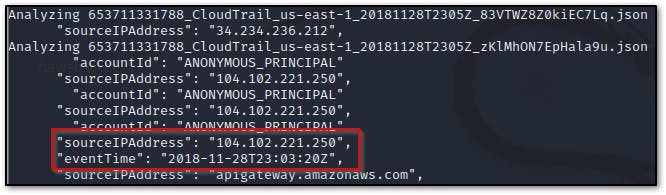
What source IP address generated the event dated 2018-11-28 at 23:03:20 UTC?
create a shell script to search all the log files for the specified date and associated source IP
#!/bin/bash LOGS="*.json" #specifying the variable for logs for l in $LOGS # starting the for loop do echo "Analyzing $l" # analyzing the log file cat "$l" | jq | grep '2018-11-28T23:03:20\|IP' donethe observed source IPs are 104.102.221.250 & 34.234.236.212
#5
Which IP address does not belong to Amazon AWS infrastructure?
ipinfo shows that 104.102.221.250 is from Akamai
ip: "104.102.221.250" hostname: "a104-102-221-250.deploy.static.akamaitechnologies.com" city: "Washington" region: "Washington, D.C." country: "US" loc: "38.8951,-77.0364" org: "AS20940 Akamai International B.V." postal: "20004" timezone: "America/New_York" asn: Object asn: "AS20940" name: "Akamai International B.V." domain: "akamai.com" route: "104.64.0.0/10" type: "isp" company: Object name: "Akamai Technologies, Inc." domain: "akamai.com" type: "isp"
#6
Which user issued the 'ListBuckets' request?
create a shell script to search all the log files for the
ListBucketAPI call!/bin/bash LOGS="*.json" #specifying the variable for logs for l in $LOGS # starting the for loop do echo "Analyzing $l" # analyzing the log file cat "$l" | jq | grep ListBuckets # finding the ListBuckets API call in any of the logss cat "$l" | jq | grep userName # grep username doneThe only JSON log file with the
ListBucketAPI call has the userName parameter of level3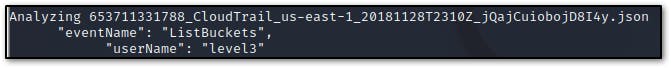
#7
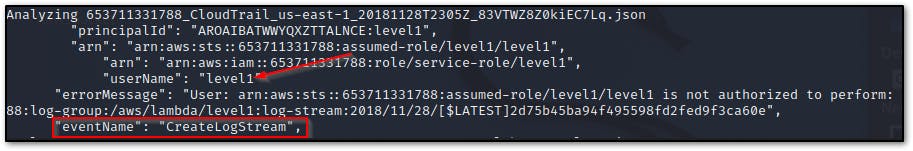
What was the first request issued by the user 'level1'?
create a shell script to search all the log files with level1 for the eventName
!/bin/bash LOGS="*.json" #specifying the variable for logs for l in $LOGS # starting the for loop do echo "Analyzing $l" # analyzing the log file cat "$l" | jq | grep level1 cat "$l" | jq | grep '"UserName": "level1"'| sort -u cat "$l" | jq | grep eventName # grep eventname donerequest observed (eventName) is
CreateLogStream